What is digital forensics?
Digital forensics, also known as computer forensics, collects and helps users present digital evidence to assist litigation.
As technology evolves, so do cybercrimes. Digital evidence stored in computers, smartphones, flash drives, or cloud storage can be corrupted or stolen. Digital forensics preserves this evidence through technology and investigative techniques.
Digital forensics software allows researchers to safely identify, collect, and store digital evidence. Digital forensics experts use this evidence in legal proceedings to assist the judiciary.
Types of digital forensics
Digital forensics recovers lost data or analyzes data evidence to discover the “why” and “how” behind a cyber attack. It’s classified into the following types:
- Media forensics includes collecting, identifying, analyzing, and presenting audio, video, or image evidence during an investigation.
- Cyber forensics covers data collection and digital evidence presentation during a cyber crime investigation.
- Mobile forensics encompasses recovering digital evidence from mobile phones, global positioning system (GPS) devices, tablets, or laptops.
- Software forensics presents evidence related to software during an investigation.
- Computer forensics collects digital evidence from computers, laptops, and other computing devices.
- Database forensics investigates any malicious activities or access to a database and analyzes any modifications. It verifies commercial contracts and investigates large-scale financial crimes.
Common digital forensic techniques
Digital forensics experts use one or more of the following techniques to collect and analyze evidence.
- Deleted file recovery: This helps recover and restore files deliberately or unknowingly deleted by a person or a virus.
- Reverse steganography: While steganography hides data within a digital message, reverse steganography is when experts look at a message's hashing. Hashing refers to a data string that changes when a file or message is interrupted.
- Cross-drive analysis: Cross-drive analysis examines data across several computer drives using concepts like correlation and cross-referencing to compare events.
- Live analysis: This analyzes a running computer’s volatile data stored in random access memory (RAM) or cache memory. It helps to identify the cause of abnormal computer traffic.
- Preserving evidence: Experts use a write blocker tool to create an exact copy of the initial data. It prevents any device or program from corrupting the original evidence.
- Web activity reconstruction: Experts use web activity reconstruction to retrieve browsing history and access temporary internet files and accepted cookies. It comes in handy when a user deletes the browsing history to plead plausible deniability.
- Network device investigation: This technique investigates all network logs. Experts use it when server logs are unavailable for unknown reasons.
- Bait tactics: It helps experts extract and copy a cyber criminal’s internet protocol (IP) address. Experts send an email to capture the recipient's IP address, allowing them to track suspected criminals.
Digital forensics steps
For digital evidence to be accepted, an expert has to follow specific steps so that the evidence is not tampered with.
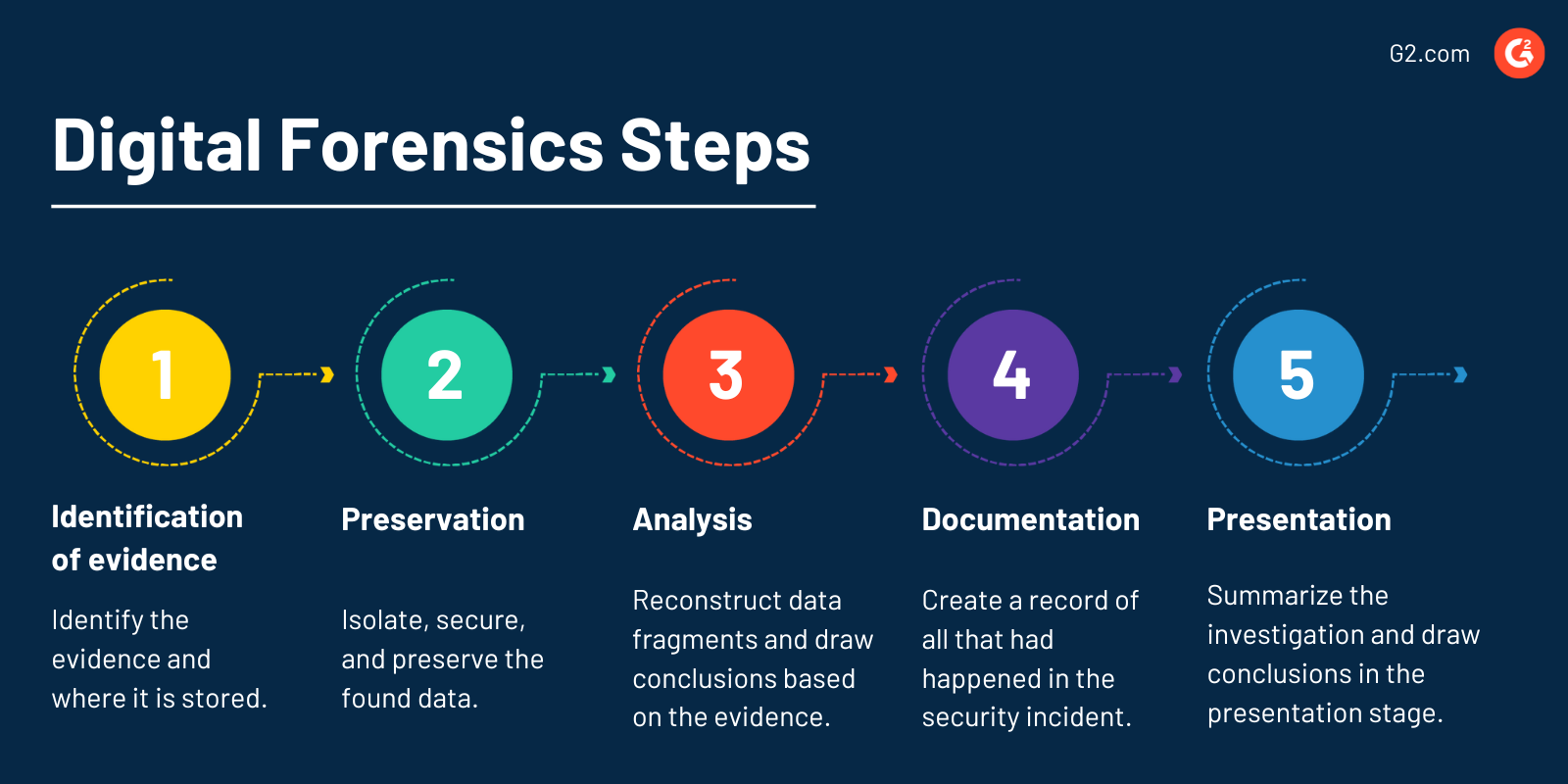
Below are the five common steps involved in a digital forensics investigation.
- Identification of evidence: Identify the evidence and where it is stored.
- Preservation: Isolate, secure, and preserve the found data. Ensure any external or internal threat cannot tamper with the data.
- Analysis: Reconstruct data fragments and draw conclusions based on the digital evidence.
- Documentation: Create a record recreating all that had happened in the security incident.
- Presentation: Summarize the entire investigation and draw a conclusion in the presentation stage.
Digital forensics vs. cyber security
Digital forensics is recovering data from a digital device to identify evidence of criminal activity. Cyber security is safeguarding online data against any threats from cyber criminals before they can happen.
Cyber security deploys tools and protocols to protect computers from cyberattacks. Professionals use information technology (IT) skills and operating system (OS) knowledge to create an unbreachable system.
Although digital forensics and cyber security may seem similar, they have unique differences. Cyber security is preventative, and digital forensics is reactive. Digital forensics doesn’t deal with preventing cybercrimes. However, it does help cyber security professionals note how a cyber crime occurred and how it can be prevented.
A digital forensics expert works with investigators to access a system’s data or with organizations to help them recover lost data. Cyber security offers specializations such as systems architecture, software security, access management, ethical hacking, etc. The main specializations offered by digital forensics are criminal investigations and data recovery.
Learn more about cybersecurity and protect organizations and enterprises against cyber attacks.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.



















