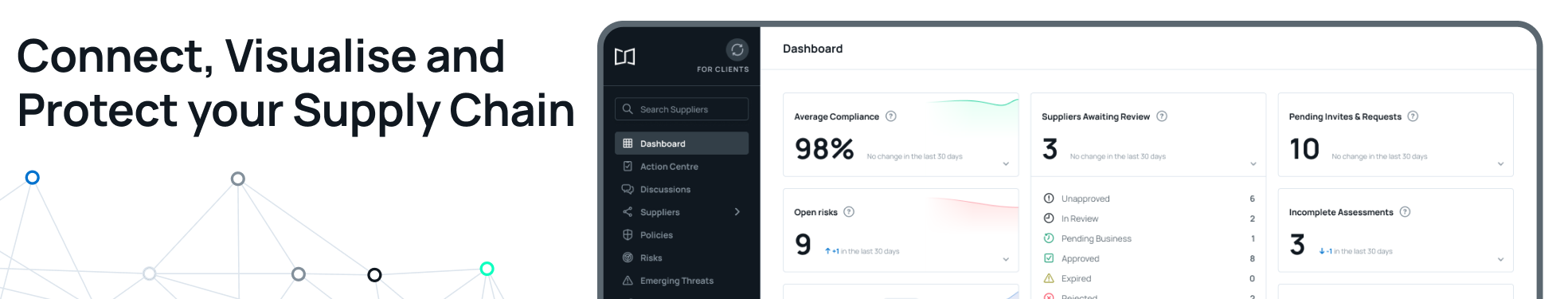
Risk Ledger Features
Functionality (12)
Risk assessment (4)
Risk Assessment (2)
Risk Control (3)
Monitoring (2)
Reporting (3)
Generative AI - Vendor Security and Privacy Assessment (2)
Agentic AI - Third Party & Supplier Risk Management (2)
Explore More
Which network management software offers the best real-time monitoring?
What is the most affordable note-taking software for teams?
Highly recommended demo automation platforms for tech sector